#Atari2600 game, Raiders of the Lost Ark source code completely disassembled and reverse engineered
Every line fully commented
#retrodev #retrogaming #atari #reverseengineering #assembler #programming #romhacking
From the retrogamedev communit...
#reverseengineering
You know you're about to have a very bad time when...
Today's Tutorial [February 8, 2026]
Lesson 104: ARM-32 Course 2 (Part 39 – Debugging Pre-Increment Operator)
This tutorial will discuss debugging pre-increment operator.
After a ton of work, I've finally gotten over my perfectionism and made https://github.com/mattst88/ip32prom-decompiler public.
It decompiles the PROM firmware for the Silicon Graphics O2 (IP32) and reassembles it into a bit-identical image.
Even if that doesn't sound interesting to you, the README and reverse-engineering document should make for a fun read.
In this video, I'm analyzing a really confusing dialog on macOS. Let's dig a bit deeper into what it should do and what it's actually doing. #reverseengineering
Today's Tutorial [February 7, 2026]
Lesson 103: ARM-32 Course 2 (Part 38 – Pre-Increment Operator)
This tutorial will discuss the pre-increment operator.
Full-Blown Cross-Assembler…in A Bash Script
https://hackaday.com/2026/02/06/full-blown-cross-assembler-in-a-bash-script/
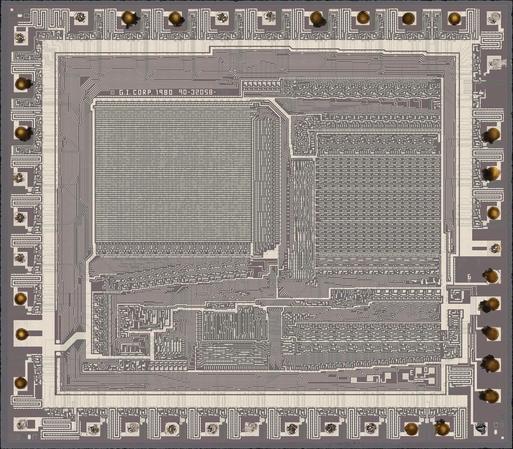
Hello! It has been a little while, but #nakeddiefriday is back in town.
Today's exhibit is an old PIC1650A. Yes, one of *the* PIC series of microcontrollers. Note it was designed by General Instrument in 1980. It was fabbed in a single metal layer, metal-gate NMOS process. The image is about 4.3x3.8 mm.
No full-res link as SP is still borked.
Solving Fossil SCM's CAPTCHA in 171 characters | nns.ee
r2agent is a tool to automate radare2 workflows through autonomous agents. #reverseengineering #ai https://github.com/nitanmarcel/r2agent
Today's Tutorial [February 5, 2026]
Lesson 101: ARM-32 Course 2 (Part 36 – Debugging SizeOf Operator)
This tutorial will discuss debugging sizeof operator.
AI can explain disassembly, but security still depends on good design.
🔐 Episode 519: Password Is All Zeros
In this episode, Elecia and Chris joined by Mark O. and James Rowley to explore:
- The fascinating world of safecracking
- How the lock industry often operates in isolation from broader security practices
- The ethics of doing a bad job when building systems meant to protect lives and property
🎧 Listen now on your favorite podcast app
📖 Read the transcript: https://embedded.com/transcripts/519
#security #engineering. #embedded #reverseengineering #cybersecurity
If you like understanding what binaries really do 👀
@rizin v0.8.2 has been released, an open-source reverse engineering framework for analyzing binaries, understanding machine code, and debugging programs 🔎
Available now on Parrot 7 🦜 Find out more here https://rizin.re/ 🔗
#ParrotSec #ParrotOS #cybersec #cybersecurity #reverseengineering #cybersecuritynews #linux #linuxdistro
Today's Tutorial [February 4, 2026]
Lesson 100: ARM-32 Course 2 (Part 35 – SizeOf Operator)
This tutorial will discuss the sizeof operator.
Patching ELFs with ~Assembly~ C, or abusing the linker for fun and profit
📬 Mit SpotiFLAC wird Spotify zur Wunschliste
#Entertainment #ReverseEngineering #Softwareentwicklung #DoubleDouble #Kofi #MusikDownloader #Qobuz #SpotiFLAC #Spotify #Tidal https://sc.tarnkappe.info/cbb350
Really nice talk with ALL the detail about how to reverse-engineer the actual circuit layout of a classic 1990s synthesiser:
https://www.youtube.com/watch?v=XM_q5T7wTpQ #39c3 #DSP #reverseengineering
Today's Tutorial [February 3, 2026]
Lesson 99: ARM-32 Course 2 (Part 34 – Hacking Double Variables)
This tutorial will discuss hacking double variables.
«Ma che cosa è cambiato da allora?»
«Perché nessuno realizza più progetti così fighi?»
... ci siamo chiesti, io e questo mio amico...
---
Beh...
Sicuramente è cambiata l'industria: ora si spinge - molto di più - sui #FreeToPlay con le #MicroTransazioni.
Perché qualcuno dovrebbe investire il proprio tempo per fare #ReverseEngineering di qualcosa che è già gratuito, per definizione?
Eppure - già all'epoca - alcuni di questi titoli erano già free-to-play: vedi, ad esempio, #Metin2.
Quindi? 🤔