第60回 Linuxカーネルのコンテナ機能 ―cgroup v2から使うメモリコントローラ(5)
https://gihyo.jp/article/2026/01/linux_containers-0060?utm_source=feed
#cgroup
tc-ematch(8) extended matches for use with "basic", "cgroup" or "flow" filters
https://man7.org/linux/man-pages/man8/tc-ematch.8.html
#HackerNews #tc-ematch #extended #matches #basic #cgroup #flow #filters #Linux
@arianvp @mdione @EduNET_LK @bustikiller Set up #nixos #flake module for a #grafana #dashboard for #cgroup data and #systemd and #psi #pressure data, see https://pastebin.com/K6e491wf
#TIL #cgroups' memory.current metric includes any #pagecache entries that a process in the #cgroup caused to be inserted, even if other processes are accessing it too.
This means that anything related to #systemd unit's memory accounting also inherits this property.
If your #emacs systemd unit reports insane memory usage (usually ~10G for me), this is why.
It's actually not emacs' fault for once ;)
#linux
#support
#help
#question
#systemd
#cgroup
#root
#uid
When su - error "Failed to connect to bus no medium found"
Investigated causes based on https://njroute22.com/failed-to-connect-to-bus-no-medium-found
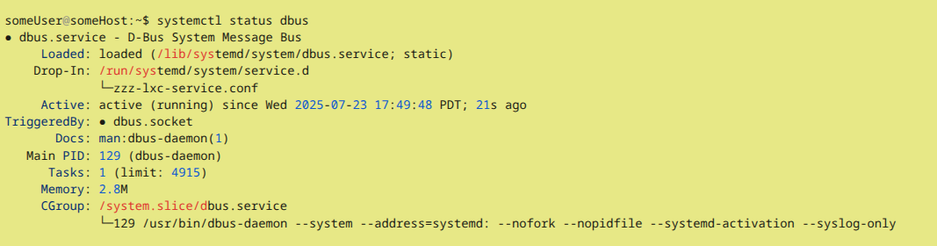
Image1: $ systemctl status dbus. "CGroup" led me to systemd control groups.
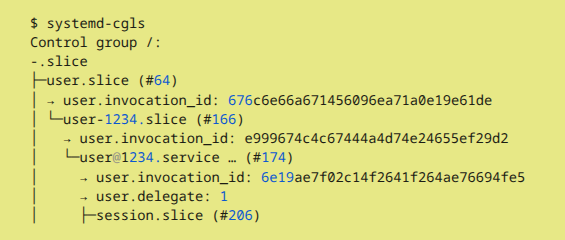
Image2: $ systemd-cgls. From entry user-1234.slice ONLY configurations for originally created host user (i.e., ID 1234 user in sudoers), BUT NO ENTRY for root (i.e., user-0)
Q: Can root be made a member of systemd control group like user-1234 is?
"#Linux #cgroup, from first principles"
« On va apprendre à limiter la mémoire, le CPU, et l'envie de hurler devant #systemd. Bref, c’est moche, c’est bas niveau, c’est Linux. Et c’est fascinant. » #RudeOps
https://fzakaria.com/2025/05/26/linux-cgroup-from-first-principles
Замедление работы pg_repack с помощью cgroup
Операция VACUUM FULL полностью пересоздаёт таблицу, предельно оптимизируя её. Она требует полной блокировки таблицы, поэтому высоконагруженные таблицы обрабатывать ею без простоя системы нельзя. Вместо VACUUM FULL можно использовать расширение pg_repack . Оно создаёт на обрабатываемой таблице триггер, отслеживающей модификации, создаёт копию таблицы, догоняет набежавшие изменения. В конце работы берётся короткая блокировка, старая таблица удаляется, новая становится на её место. Недостатком pg_repack является то, что она работает СЛИШКОМ БЫСТРО – фактически данные копируются и удваиваются в объёме (по отношению к исходной таблице). Каталог pg_wal забивается с такой скоростью, что архиватор не успевает обрабатывать файлы. Далее описывается способ замедления работы pg_repack с использованием механизма cgroup .
Awesome. Can't read the documentation. Thanks #RedHat
https://access.redhat.com/articles/3735611
#cgroup migration
Ok writing some #eBPF which hooks onto a #cgroup and limits its network access while leaving the rest of the host unaffected, this is fun! Bit of #c and #golang
Using
- https://ebpf-go.dev/guides/getting-started/#the-go-application
- https://nfil.dev/coding/security/ebpf-firewall-with-cgroups/
Next, a #container is a #cgroup of processes running in their own PID namespace. This cgroup is cleaned up when the container is stopped. Any zombies that are in a container are removed on stop. They don't reach the hosts init.
10/n
Systemd future feature removals:
* Support for System V service scripts is now deprecated and will be removed in a future release.
* We intend to remove cgroup v1 support from a systemd release after the end of 2023.
Another week - a new troubleshooting case. And it's only Monday...
Simply executed the widely used htop command in a #Debian 12 (Bookworm) #LXC container and saw all the physical cpu cores from the host - even though #cgroup limits are set.
First expected a bug in LXC/lxcfs or cgroup handling in Bookworm but it turns out that htop itself seems to show a wrong cpu count...
Bug? Regression? Feature? Not sure yet...
第54回 Linuxカーネルのコンテナ機能 ―cgroup v2から使うCPUの帯域幅制限(2)
https://gihyo.jp/article/2023/11/linux_containers-0054?utm_source=feed
#gihyo #技術評論社 #gihyo_jp #Linux #コンテナ #cgroup #CPUコントローラ
Kroniki Shodana: Docker cz.II ( https://nfsec.pl/pentest/6230 ) #docker #security #cgroup #linux #twittermigration
When a #Linux System #Container is unable to start, there can be a couple of reasons.
By forwarding the #LXC start log into a file and increase the loglevel, the real errors can (usually) be identified.
In this particular situation a wrong CPU number was added into the LXC's #cgroup limit configuration. A typical human counting vs. machine counting error. 😅
https://www.claudiokuenzler.com/blog/1299/lxc-container-unable-to-start-failed-setup-cgroup-limits