In your org, what’s harder: tracking 100+ CVEs from a monthly patch cycle or implementing a consistent patch policy?
Learn about major recent CVEs like CVE-2026-20805 here:
👉 https://cvedatabase.com/cve/CVE-2026-20805 #CyberAwareness #SecurityOps
#SecurityOps
The Linux CUPS vulnerability was a zero-day that presented a critical question: how would you prepare if you knew a vulnerability existed but didn't know the details? Our on-demand webinar explores how an SBOM-powered approach turns this puzzle into a straightforward, actionable plan.
📚Learn how to move from discovery to remediation planning in minutes. Watch the full video here: https://go.anchore.com/rapid-incident-response-with-sboms/ #Cybersecurity #SBOM #Linux #ZeroDay #SecurityOps
A breach is not only a security issue. It is an operations issue. #IBM puts the average at $4.4M. The practical lesson for 2026 is to automate the basics: identity hygiene, alert triage, and response runbooks so teams contain faster and spend less.
#Cybersecurity #SecurityOps #Automation #RiskManagement #MSP
New analysis reveals a Silver Fox operation using a fake Microsoft Teams installer to deploy ValleyRAT in attacks targeting China-based users.
The campaign mixes SEO poisoning, Cyrillic false-flag elements, DLL injection, and BYOVD techniques - making detection and attribution more challenging.
Researchers also note a secondary chain using a trojanized Telegram installer.
What’s your perspective on increased abuse of trusted-app installers in malware campaigns?
Source: https://thehackernews.com/2025/12/silver-fox-uses-fake-microsoft-teams.html
💬 Join the discussion
👍 Boost & follow for more threat intelligence
#CyberSecurity #ThreatIntel #ValleyRAT #SilverFox #InfoSec #MalwareResearch #SecurityOps #CyberThreats
🚨 NEW BLOG POST 🚨
"The Breaking Point: Why Cybersecurity and SOC Professionals Are Burning Out—And What Actually Works"
Nearly half of cybersecurity professionals experience moderate to severe burnout. 65% of SOC analysts have seriously considered leaving. But here's the thing: it's not a resilience problem. It's a design problem.
I've written a comprehensive breakdown of:
✓ Why the 10,000+ daily alerts trap is unsustainable
✓ How 24/7 shifts destroy sleep and performance
✓ Why compensation alone won't fix retention
✓ Practical solutions: fatigue management, alert rationalization, career paths, and organizational culture
This isn't about yoga classes and "self-care." It's about fixing the structural issues that burn through talent faster than the industry can train replacements.
Read the full post with research-backed strategies for both individuals and organizational leaders:
#Cybersecurity #SOC #Burnout #MentalHealth #InfoSec #SecurityOps #CareerDevelopment #Workforce
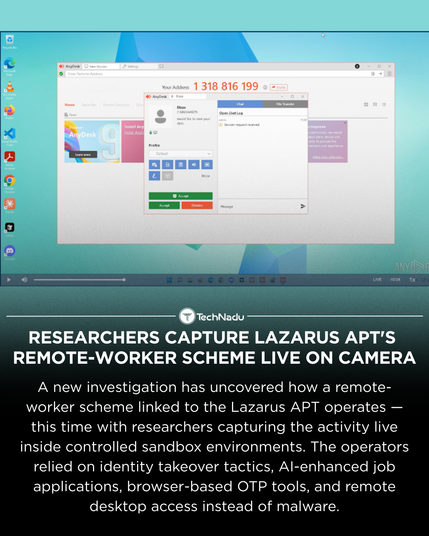
Researchers have documented a remote-worker infiltration workflow linked to the Lazarus APT by observing operators live inside ANY.RUN sandboxed “developer laptops.”
The sessions revealed identity-driven tooling, AI-assisted interviews, Chrome profile syncing, OTP utilities, and remote desktop access - all without traditional malware deployment.
How should defenders adapt hiring-related threat models to account for identity takeover and remote access–driven APT tradecraft?
Source: https://thehackernews.com/2025/12/researchers-capture-lazarus-apts-remote.html
Follow us for more continuous threat-intel coverage.
#Infosec #CyberSecurity #ThreatIntel #APT #RemoteWork #IdentitySecurity #TechNadu #DigitalSafety #SecurityOps #ThreatHunting
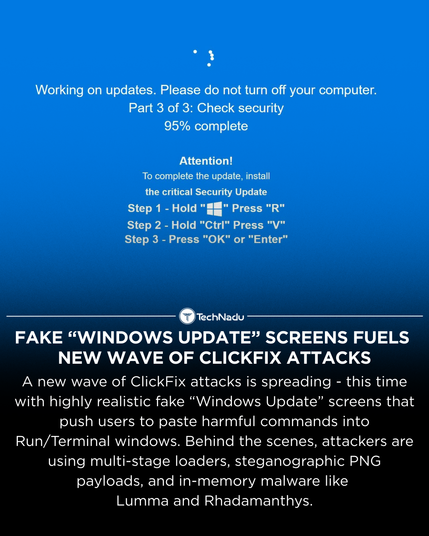
ClickFix operators are now using fake full-screen “Windows Update” pages to push victims into running malicious commands. Combined with steganographic loaders and in-memory execution, these campaigns continue to evolve.
What detection or user-training approach do you think works best today?
Source: https://www.helpnetsecurity.com/2025/11/25/fake-windows-update-screen-clickfix/
Follow @technadu for ongoing threat-intel breakdowns and practical defense insights.
#Infosec #ThreatIntel #ClickFix #EDR #CyberHygiene #MalwareTrends #SecurityOps #WindowsSecurity #InfoStealer
DoorDash has confirmed a data breach following a targeted social engineering attack against an employee. The incident exposed non-financial personal data (names, emails, phone numbers, addresses), with no payment or government ID data affected.
DoorDash notified users, involved law enforcement, and strengthened internal controls. Social engineering remains the dominant vector across 2025 incidents — consistent with recent Extortion-as-a-Service trends.
#Cybersecurity #DoorDash #Infosec #ThreatIntel #SocialEngineering #SecurityOps #DataProtection
DOJ announces new actions targeting illicit DPRK-linked schemes, including identity fraud enabling remote IT work at 136+ U.S. companies and APT38 crypto heists exceeding $15M.
Key elements:
• Multiple guilty pleas (U.S. & international)
• Unauthorized remote access + identity misuse
• Cryptocurrency laundering + ongoing seizure efforts
• DOJ, FBI & NSD coordination under DPRK RevGen initiative
Thoughts on improving remote-work identity vetting?
👍 Follow for more verified, unbiased cyber reporting.
#infosec #APT38 #Cybercrime #ThreatIntel #DOJ #NorthKorea #SecurityOps #CyberPolicy #DigitalForensics
AI is becoming central to security operations. Let's talk about why. 👇
AI-assisted workflows are on the rise. ⬆️ And, when an algorithm highlights a critical #security event, analysts need to understand why that happened. Without true visibility, this #AI assistance risks creating new blind spots and hiding important context, rather than leading to a solution. 😓
To make sense of the constant overflow of alerts, you need AI capabilities that are built into workflows that you already use, like:
☑️ Behavioral detection
☑️ Risk-based prioritization
☑️ Investigation summaries
☑️ Smarter dashboards and search
Learn how you can leverage these important AI capabilities and stay in control while using tools that accelerate detection, streamline investigations, and strengthen your reporting: https://graylog.org/post/how-graylog-uses-explainable-ai-to-help-security-teams/ #cybersecurity #securityops #security #securityanalyst
🚨 SonicWall VPN Alert
Huntress has reported a widespread compromise impacting over 100 accounts across 16 organizations. Attackers used valid credentials to gain access, some performing lateral movement and reconnaissance - possibly linked to Akira ransomware operations.
💬 How does your team mitigate credential-based VPN attacks? Comment below & follow @technadu for actionable threat intelligence.
#CyberSecurity #SonicWall #VPN #Ransomware #AkiraRansomware #PatchManagement #ThreatIntelligence #NetworkSecurity #Infosec #CyberAwareness #SecurityOps #TechNadu
175 malicious npm packages + unpkg CDN used as resilient phishing infrastructure (26k downloads).
Attack strategy: automated package publishing → CDN-served JS redirects with victim email fragments → pre-filled credential harvesters. This is a hosting-abuse supply-chain tactic (registry+CDN), not a typical dependency compromise.
Immediate defensive steps:
• Monitor npm publish frequency and automation patterns.
• Alert on unpkg asset requests tied to newly published/empty package manifests.
• Treat HTML attachments as high risk; validate source and block local file URIs in email clients.
Discuss mitigation strategies below and follow @technadu for more threat intelligence.
#InfoSec #ThreatIntel #npm #unpkg #Phishing #SupplyChainSecurity #DevSecOps #SecurityOps #ThreatHunting #CyberSecurity
🚨 The next zero-day is coming. The only question is how your #security team will react. Our on-demand webinar with Anchore experts shows how comprehensive SBOM tracking turns a chaotic scramble for information into an organized, data-driven response.
➡️ Don't get left behind. Watch and learn how to prepare: https://go.anchore.com/rapid-incident-response-with-sboms/ #SBOM #IncidentResponse #SecurityOps
The Linux CUPS vulnerability was a zero-day that presented a critical question: how would you prepare if you knew a vulnerability existed but didn't know the details? Our on-demand webinar explores how an SBOM-powered approach turns this puzzle into a straightforward, actionable plan.
📚Learn how to move from discovery to remediation planning in minutes. Watch the full video here: https://go.anchore.com/rapid-incident-response-with-sboms/ #Cybersecurity #SBOM #Linux #ZeroDay #SecurityOps
Where are the #CheckPoint #Firewall administrators in the #fediverse? 🔎
Let's connect for discussing various topics. 💬
I'm also active in the #CheckMates community: https://community.checkpoint.com/
#QuantumFirewall #QuantumManagement #SmartConsole #SecurityOps #CyberSecurity #InfoSec #NetworkSecurity
Hot off the #CheckMates Press! Quantum Management Spotlight – Discover 3 Features You Should Start Using Today!
Get ready to boost your SecOps with tools designed to save time, reduce risk, and make your life easier. Here’s what’s covered:
- Network Feed
- Dynamic Log Distribution
- SmartWorkflow
Read the full post on CheckMates: https://community.checkpoint.com/t5/Management/This-Month-s-Spotlight-3-Features-You-Should-Start-Using-Today/td-p/252359
#CheckPoint #QuantumManagement #SmartConsole #CheckMates #SecurityOps #CyberSecurity #NetworkSecurity
A comprehensive look at EDR systems' inner workings and the real-world tactics employed to circumvent them. Essential information for professionals involved in security operations and threat analysis.
Grounded in tested techniques—not speculation—and focused on practical tradecraft.
🔥 70,000+ CVEs reported yearly.
You need more than a list.
You need:
✅ Prioritization
✅ Context
✅ Action
Vulnerability management should reduce noise, not add to it.
#Infosec #SecurityOps
Logs aren't just storage—they're sanity-savers! 🧠
Less noise, more clarity, happier analysts. Our "Ultimate Guide to Log Optimisation" helps teams boost productivity, catch real threats faster, and reduce burnout.
Get your free copy now 👉 https://zcu.nu/tUB
#AnalystProductivity #Pebble #LogOptimisation #AI #SecurityOps @pebbleTek
Drowning in CISA advisories? Tines has a free workflow automating monitoring, enrichment (CrowdStrike), & ticketing (ServiceNow) via Slack approvals. Cut manual tasks by 60% & keep analysts focused.
#SecurityOps #Automation #InfoSec