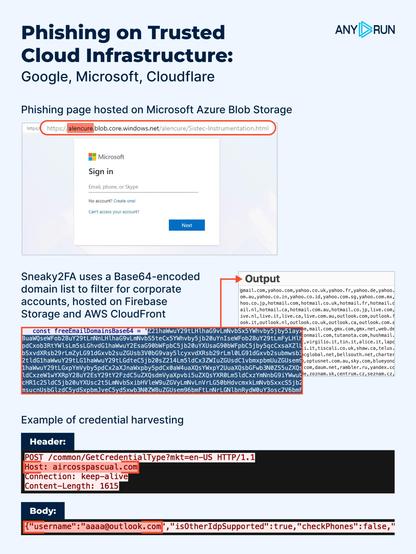
🚨 Attackers Took Over a Real Enterprise Email Thread to Deliver #Phishing
⚠️ The hacker replied directly within an active discussion among C-suite executives about a document pending final approval, sharing a phishing link to a fake Microsoft authentication form.
The attackers likely compromised a sales manager account at an enterprise contractor and hijacked a trusted business conversation.
👾 By detonating samples in the #ANYRUN Sandbox and pivoting indicators in TI Lookup, we uncovered a broader campaign powered by the #EvilProxy phishkit. The activity has been ongoing since early December 2025, primarily targeting companies in the Middle East.
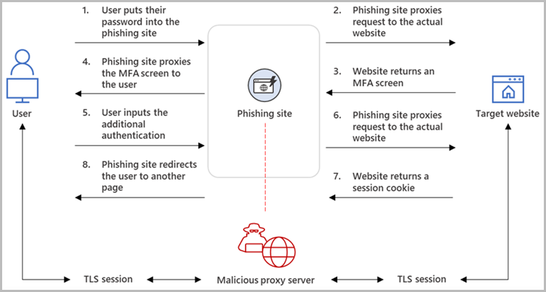
🔗 Execution chain:
SCA phishing email ➡️ 7 forwarded messages ➡️ Phishing link ➡️ Antibot landing page w/ Cloudflare Turnstile ➡️ Phishing page w/ Cloudflare Turnstile ➡️ EvilProxy
❗️ Supply chain phishing campaigns now rely on layered social engineering, real conversation hijacking, and infrastructure that closely resembles #PhaaS platforms in both complexity and scale. These attacks exploit business trust, not technical vulnerabilities.
🎯 How companies can reduce supply chain phishing risk:
🔹 Flag HTML/PDF files with dynamic content, review unusual approval flows, and detonate suspicious files in a sandbox before interaction.
🔹 Split responsibility between initiating and approving document or process changes. Apply the four-eyes principle.
🔹 Use realistic supply chain attack scenarios and “perfect-looking” emails in awareness programs.
⚡️ Further technical insights are coming, stay tuned!
With #ANYRUN Sandbox, the threat's full attack chain becomes visible through real behavior and actionable reports with IOCs in under 60 seconds, significantly cutting MTTD and MTTR. Security teams triage faster, reduce Tier-1 overload and escalations, and contain incidents earlier to limit business impact.
👨💻 Equip your SOC with stronger phishing detection: https://any.run/enterprise/?utm_source=mastodon&utm_medium=post&utm_campaign=b2b_social_engineering_phishing&utm_term=270126&utm_content=linktoenterprise
#ExploreWithANYRUN
📋 IOCs:
URI pattern: POST ^(/bot/|/robot/)$
Domains:
himsanam[.]com
bctcontractors[.]com
studiofitout[.]ro
st-fest[.]org
komarautomatika[.]hu
eks-esch[.]de
avtoritet-car[.]com
karaiskou[.]edu[.]gr
Domain pattern: ^loginmicrosoft*
#cybersecurity #infosec



![Zoomed in screenshot of hxxps://large-listening-838836.framer[.]app (this site is still live).
A fake login page for Luxembourg asking for:
1. user-ID
2. password
3. TOTP code](https://files.mastodon.social/cache/media_attachments/files/115/803/966/739/104/979/small/1219d602b07758ef.jpg)