Top 10 last week's threats by uploads 🌐
⬆️ #Agenttesla 549 (306)
⬇️ #Asyncrat 435 (443)
⬆️ #Dcrat 379 (225)
⬇️ #Xworm 366 (435)
⬇️ #Stealc 360 (475)
⬇️ #Vidar 345 (455)
⬆️ #Salatstealer 235 (206)
⬇️ #Remcos 234 (307)
⬆️ #Gh0st 225 (166)
⬇️ #Quasar 200 (207)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=090226&utm_content=linktoregister#register
#AsyncRAT
Top 10 last week's threats by uploads 🌐
⬆️ #Stealc 475 (311)
⬆️ #Vidar 456 (309)
⬆️ #Asyncrat 444 (360)
⬇️ #Xworm 435 (861)
⬆️ #Remcos 307 (277)
⬆️ #Agenttesla 307 (157)
⬆️ #Reverseloader 303 (143)
⬆️ #Dcrat 227 (88)
⬇️ #Quasar 208 (233)
⬇️ #Salatstealer 206 (221)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=020226&utm_content=linktoregister#register
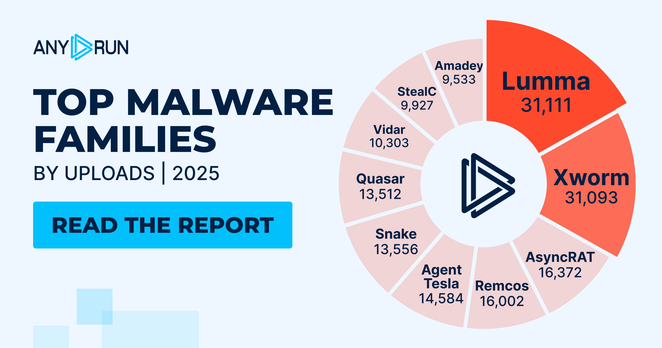
⚠️ In 2025, #Lumma led detections with 31K+ cases, while #XWorm saw sharp growth, up 4.3x year over year.
#AsyncRAT and #Remcos followed with ~16K detections each, while #Quasar and #Vidar entered the top list, signaling renewed RAT and stealer diversification.
📈 Learn more in our 2025 threat landscape report: https://any.run/cybersecurity-blog/malware-trends-2025/?utm_source=mastodon&utm_medium=post&utm_campaign=malware_trends_25&utm_term=270126&utm_content=linktoblog
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 861 (712)
⬆️ #Asyncrat 360 (337)
⬆️ #Stealc 311 (307)
⬆️ #Vidar 309 (266)
⬆️ #Remcos 278 (248)
⬆️ #Quasar 233 (209)
⬇️ #Gh0st 192 (218)
⬆️ #Lumma 187 (140)
⬆️ #Agenttesla 157 (135)
⬆️ #Reverseloader 143 (111)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=260126&utm_content=linktoregister#register
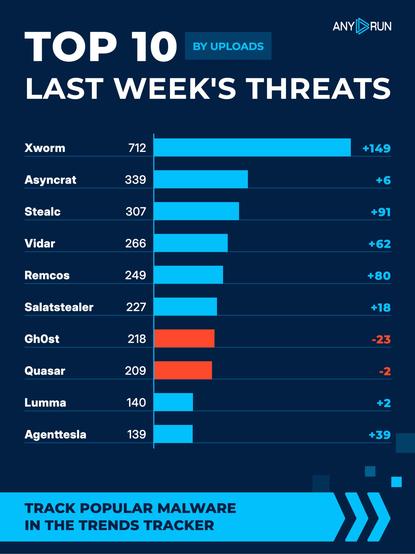
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 712 (563)
⬆️ #Asyncrat 339 (333)
⬆️ #Stealc 307 (216)
⬆️ #Vidar 266 (204)
⬆️ #Remcos 249 (169)
⬆️ #Salatstealer 227 (209)
⬇️ #Gh0st 218 (241)
⬇️ #Quasar 209 (211)
⬆️ #Lumma 140 (138)
⬆️ #Agenttesla 139 (100)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=190126&utm_content=linktoregister#register
🪝 We tracked a #phishing campaign against Germany's largest manufacturing enterprise.
It abuses a CVE, delivers #AsyncRAT, and has a low detection rate among most AV engines.
Get actionable intel to detect it early 👇
https://any.run/cybersecurity-blog/german-manufacture-attack/?utm_source=mastodon&utm_medium=post&utm_campaign=german_manufacture_attack&utm_term=140126&utm_content=linktoblog
Attackers Abuse #Python, #Cloudflare to Deliver #AsyncRAT
The #phishing campaign shows how attackers continue to weaponize legitimate #cloud services and #opensource tools to evade detection and gain trust.
https://www.darkreading.com/endpoint-security/attackers-abuse-python-cloudflare-deliver-asyncrat
#security
Analyzing a Multi-Stage AsyncRAT Campaign via Managed Detection and Response
Pulse ID: 69671d2d346e3755fbc010af
Pulse Link: https://otx.alienvault.com/pulse/69671d2d346e3755fbc010af
Pulse Author: Tr1sa111
Created: 2026-01-14 04:35:57
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AsyncRAT #CyberSecurity #InfoSec #OTX #OpenThreatExchange #RAT #bot #Tr1sa111
Analyzing a Multi-Stage AsyncRAT Campaign via Managed Detection and Response
Threat actors exploited Cloudflare's free-tier infrastructure and Python environments to deploy AsyncRAT, demonstrating advanced evasion techniques. The attack begins with phishing emails containing Dropbox links to malicious files. It uses legitimate Python downloads and sophisticated code injection targeting explorer.exe. The campaign ensures persistence through multiple vectors, including startup folder scripts and WebDAV mounting. It abuses trusted infrastructure like Cloudflare to mask activities and evade detection. The attackers employ social engineering tactics, such as displaying legitimate PDF documents, to reduce suspicion. This campaign highlights the trend of abusing cloud services for malware delivery and execution, emphasizing the need for multi-layered security approaches.
Pulse ID: 696559e4cecb38ddf228e296
Pulse Link: https://otx.alienvault.com/pulse/696559e4cecb38ddf228e296
Pulse Author: AlienVault
Created: 2026-01-12 20:30:28
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#AsyncRAT #Cloud #CodeInjection #CyberSecurity #Dropbox #Email #ICS #InfoSec #Malware #OTX #OpenThreatExchange #PDF #Phishing #Python #RAT #Rust #SocialEngineering #bot #AlienVault
⚠️ In Q4 2025, #XWorm surged 174%, fueled by its flexibility across manufacturing and healthcare
#AsyncRAT and #Quasar followed with 46% and 27% growth, showing open-source RATs outpacing commercial stealers
📈 Learn more in our threat landscape report: https://any.run/cybersecurity-blog/malware-trends-report-q4-2025/?utm_source=mastodon&utm_medium=post&utm_campaign=malware_trends_report_q4_2025&utm_term=130126&utm_content=linktoblog
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 563 (350)
⬆️ #Asyncrat 335 (176)
⬆️ #Warzone 289 (35)
⬆️ #Gh0st 241 (14)
⬆️ #Stealc 216 (180)
⬆️ #Quasar 211 (159)
⬆️ #Vidar 204 (184)
⬆️ #Remcos 169 (40)
⬇️ #Lumma 139 (167)
⬆️ #Reverseloader 108 (21)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=120126&utm_content=linktoregister#register
@malware_traffic Thank you for sharing Brad!
The TLS traffic to 173.232.146.62:25658 looks like #AsyncRAT or possibly #PureRAT. Can you confirm if it was generated by the powershell script with MD5 90389d2988cce2fe508087618dd2f519 from fnjnbehjangelkd[.]top?
A domain registration is more like a lease rather than a deed. You get the exclusive right to use a domain name for a fixed term, but if you miss renewal, someone else can swoop in. What's scary is that with dropcatch services, cybercriminals can automate monitoring of pending‑delete domains and fire off registrations the split‑second a name is deleted by the registry and becomes available again. Think hawks circling for high‑value prey. 🦅
That's what happened to fita[.]org, a popular website owned by the Federation of International Trade Associations (FITA) and referenced by many government bodies including the International Trade Administration (trade.gov). The domain now sits behind Cloudflare and functions as a command-and-control (C2) for the AsyncRAT malware. The actor controlling it also stood up these C2 endpoints:
90phutif[.]cc,90phutis[.]cc,90phutiv[.]cc,90phuttn[.]cc,xoilaclinkf[.]cc,xoilactivi[.]uk,xoilactivik[.]cc,xoilactivil[.]cc,xoilactivim[.]cc,xoilactivin[.]cc,xoilactivio[.]cc,xoilactivip[.]cc,xoilactiviq[.]cc,xoilactivir[.]cc,xoilactivis[.]cc,xoilactivit[.]cc,xoilactiviu[.]cc,xoilactiviv[.]cc,xoilactiviw[.]cc,xoilactivix[.]cc,xoilactiviy[.]cc,xoilactiviz[.]cc,xoilacvnnc[.]tv,xoilacvnnf[.]tv,xoilacvzb[.]cc,xoilacvzc[.]cc,xoilacvze[.]cc,xoilacvzi[.]cc,xoilacvzk[.]cc,xoilacvzn[.]cc,xoilacvzp[.]cc,xoilacvzq[.]cc,xoilacvzz[.]cc,xoilacyys[.]cc,xoilaczc[.]mobi,xoilaczzbb[.]cc,xoilaczzczz[.]tv,xoilaczzdd[.]cc,xoilaczzdzz[.]tv,xoilaczziz[.]tv,xoilaczzszz[.]tv,xoilaczzvzz[.]tv
So make sure to set auto pay for any valuable domains you possess 💳 otherwise you could risk losing them. Proactive IT governance is also part of security.
#InfobloxThreatIntel #dns #async #threatintel #threatintelligence #infosec #cybersecurity #cybercrime #infoblox #rat #asyncrat #malware #dropcatch #domain #cloudflare #remoteaccesstrojan #infostealer #c2
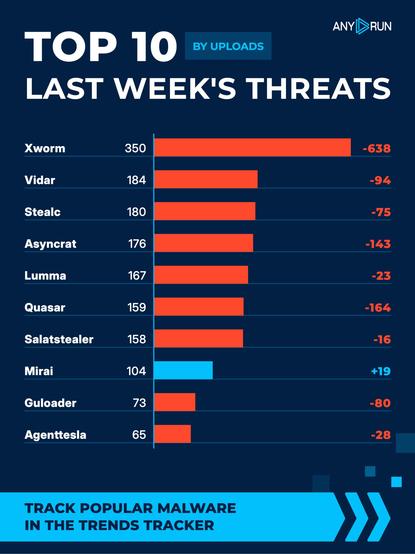
Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 350 (988)
⬇️ #Vidar 184 (278)
⬇️ #Stealc 180 (255)
⬇️ #Asyncrat 176 (319)
⬇️ #Lumma 167 (190)
⬇️ #Quasar 159 (323)
⬇️ #Salatstealer 158 (174)
⬆️ #Mirai 104 (85)
⬇️ #Guloader 73 (153)
⬇️ #Agenttesla 65 (93)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=050126&utm_content=linktoregister#register
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 988 (549)
⬇️ #Quasar 323 (353)
⬆️ #Asyncrat 319 (244)
⬇️ #Vidar 278 (282)
⬆️ #Stealc 255 (220)
⬇️ #Lumma 190 (221)
⬆️ #Gravityrat 188 (46)
⬆️ #Salatstealer 174 (95)
⬇️ #Guloader 153 (197)
⬇️ #Smoke 138 (148)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=291225&utm_content=linktoregister#register
I finished compiling the information for #Kongtuke #ClickFix activity using the finger command on 2025-12-11, and it's now live at www.malware-traffic-analysis.net/2025/12/11/index2.html
I'd already posted the #SmartApeSG ClickFix activity using finger that same day, so now both are available.
I had to run the ClickFix command on a physical host because the C2 server didn't like me when I initially tried it on a VM.
Post-infection traffic looks like the same type of #AsyncRAT I've seen before, and some Tor traffic from whatever the follow-up malware is.
It's a 221 MB zip archive containing the #pcap for the full infection, and it's about the same size as the zip archive containing forensic artifacts from the infected host.
Top 10 last week's threats by uploads 🌐
⬇️ #Xworm 550 (944)
⬇️ #Quasar 354 (364)
⬇️ #Vidar 282 (371)
⬇️ #Asyncrat 247 (396)
⬇️ #Lumma 222 (284)
⬇️ #Stealc 221 (354)
⬆️ #Guloader 197 (181)
⬆️ #Agenttesla 186 (172)
⬇️ #Smoke 148 (153)
⬇️ #Remcos 128 (212)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=221225&utm_content=linktoregister#register
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 944 (870)
⬇️ #Asyncrat 396 (413)
⬆️ #Vidar 371 (318)
⬇️ #Quasar 364 (395)
⬆️ #Stealc 354 (266)
⬆️ #Lumma 284 (282)
⬇️ #Remcos 213 (269)
⬆️ #Guloader 181 (179)
⬆️ #Agenttesla 173 (141)
⬇️ #Smoke 153 (158)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=151225&utm_content=linktoregister#register
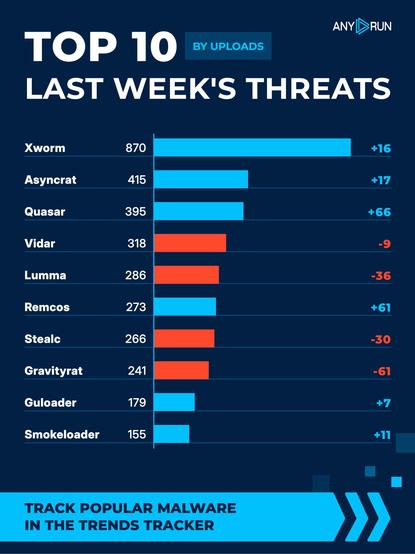
Top 10 last week's threats by uploads 🌐
⬆️ #Xworm 870 (854)
⬆️ #Asyncrat 415 (398)
⬆️ #Quasar 395 (329)
⬇️ #Vidar 318 (327)
⬇️ #Lumma 286 (322)
⬆️ #Remcos 273 (212)
⬇️ #Stealc 266 (296)
⬇️ #Gravityrat 241 (302)
⬆️ #Guloader 179 (172)
⬆️ #Smokeloader 155 (144)
Explore malware in action: https://app.any.run/?utm_source=mastodon&utm_medium=post&utm_campaign=top_ten&utm_term=081225&utm_content=linktoregister#register