Everywhere...
Day 1 at the FOSDEM ....
OMG @braillerap just gifted us an English and a German #Braille version of "Ada & #Zangemann - A Tale of Software, Skateboards and Raspberry Ice Cream". 🤗
It is the first complete book printed this way with #FreeSoftware (#OpenSource) and #Openhardware 🥰
We will have a copy at the @fsfe booth during #Fosdem and @nicorikken will cover the story in our talk on Sunday at 14 https://fosdem.org/2026/schedule/event/R9Q9ZP-ada-zangemann-bestseller-automation/ Big thank you!! 👏
I like the list, really nice.
For DNS and domain registration, have you checked out DeSec 🇩🇪? I use them for quite a while and I am very happy.
Also, for Hardware security keys, ... I know Yubikeys are the most promoted ones. But check out Token2 🇨🇭. They support all the fido2 features with 300 passkeys, openpgp, totp, .... And the price is nearly half of a Yubikey.
* https://blog.tinned-software.net/framework-expansion-card-for-token2-t2f2-security-key/
* https://blog.tinned-software.net/fido2-security-key-login-for-id-austria/
Finally finished the #Framework expansion card design for the #Token2 FIDO2 security key.
https://blog.tinned-software.net/framework-expansion-card-for-token2-t2f2-security-key/
https://www.token2.swiss/site/page/blog?p=posts/95
Find my project mentioned on the Token2 blog. 😊
Second release of the Framework expansion card adapter for Token2 T2F2 security keys. Now also supporting R3 devices.
https://codeberg.org/gerhard-tinned/Token2-Framework-ExpansionCard
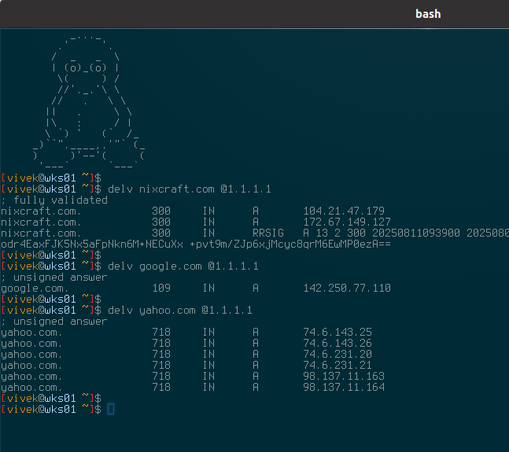
DNSSEC uses digital signatures to verify the authenticity of DNS data. It's needed for a domain to prevent attackers from hijacking traffic through DNS spoofing or cache poisoning. DNSSEC ensures that when a user looks up your domain, they are directed to the correct IP address and not a malicious, fraudulent site or recoreds. So how do you verify DNSSEC enabled or validated? Simply run:
delv domain-name-tld
delv domain @8.8.8.8
For more info see https://www.cyberciti.biz/faq/unix-linux-test-and-validate-dnssec-using-dig-command-line/
https://www.token2.com/site/page/using-token2-pin-fido2-keys-with-id-austria
Token2 published an article based on my testing and article.
See the reference to https://blog.tinned-software.net/fido2-security-key-login-for-id-austria/ the end of the page.
https://blog.tinned-software.net/fido2-security-key-login-for-id-austria/
Recently added support for new hardware security keys was added to ID-Austria.
On March 12, 1989, Tim Berners-Lee submitted a proposal for an information management system to his boss at CERN. “Vague but exciting” was his feedback. The project later became the World Wide Web.
Thank you, Sir Tim Berners-Lee, for changing the world!
Published another Article about FIDO2 hardware security keys. This is a bit of a critical view.
https://blog.tinned-software.net/security-keys-and-open-source/
My newest topic I am trying to understand better: #GNSS
While trying to write about #NTP as well as #PTP another world opened up as well. Global Navigation Satellite System or #GNSS which is most often the source of time. Digging through the different Satellite constellations #GPS , #GALILEO , #BAIDU , #GLONASS and understanding the differences was interesting.
I am still digging deeper. Anyone with knowledge, is highly welcome to educate me. ☺️👍
I came across Headlines trying to introduce fear of #FIDO2.
"Using MITM to bypass FIDO2 phishing-resistant protection" and "Passwordless Authentication Standard FIDO2 Flaw Let Attackers Launch MITM Attacks" seem very frightening. So I took a closer look into those articles.
https://www.silverfort.com/blog/using-mitm-to-bypass-fido2/
https://gbhackers.com/fid02-mitm-vulnerability/
They seem very much identical down to the fact they use the same illustrations. My understanding is that the demonstrated "#MITM #Attack" is actually an attack on the session coockie. So The idea is to let the #FIDO2 #Authentication take place uninterrupted and when successful, intercept the Session cockie when sent from the Relaying Party/Webserver to the client.
Maybe someone with a better understanding of the Standards can correct me but this attack looks to me as if it only attackls the session information which would be possible no mather what authentication would be used. In my understanding, secure session handling is a real thread but outside of the actual FIDO2 scope.
What do you think? Is it FIDO2 related? Or just a generic Session hijacking that happens to work besides others also with FIDO2 authentications?
#DNS and #DNSSEC
https://blog.tinned-software.net/dns-and-dnssec/
I have the feeling many misunderstand what DNSSEC is trying to achieve. I hope this clears it up. ☺️
“Ada & Zangemann is not only a utopian and charming story about Free Software and computers, but it is one about self-empowerment and also about joy in technology. … it may well be an eye-opener for adults, too.”
~ Dr. Constanze Kurz, Spokesperson, Chaos Computer Club (@CCC)
I have just published my next article related to #fido #securitykeys and how they can be managed in the #commandline
https://blog.tinned-software.net/fido2-security-key-management-via-commandline/
It's #FreeSoftware Day and we sat down with Matthias Kirschner (@kirschner) from FSFE (@fsfe) to talk about his children's book "Ada & Zangemann - A Tale of Software, Skateboards, and Raspberry Ice Cream" Learn more about how a young girl is taking on big tech in our interview: https://blog.torproject.org/i-love-free-software-day-interview-fsfe/ 💜💜