Founder of HACKTIVATE LABS — AI + Offensive Security studio.
Building autonomous agents, red-team tooling & secure automation systems.
⚡ AI Workflow Engines
⚔️ Penetration Testing / Cyber Defense
🔐 Web3 & Smart Contract Audits
📡 Private Mesh Networks / LoRa / VoIP
➡️ Turning vulnerabilities into velocity.
You can @mention collaborators or use #AI, #Cybersecurity, #RedTeam, #Automation
https://youtube.com/shorts/O1K23YA-5zs?si=WL9QouFgeGKLb9jX Absolutely. If you need support with marketing campaigns, sponsorship opportunities, or promotional initiatives, @vitablendsupplements, @lamedianation, @hacktivatenetwork, and @thecorporatefoo are committed to empowering youth and championing second-chance advancement.
Check out this amazing AI video creation platform! https://www.aivideo.com/onboarding?ref=5oSPjNbaR3E9nXaiWzR2fyJwolIz9WeU
Exciting RustConf 2026 updates!
📣 CFP opens this month
🌍 Visa letters available now
🏛 Returning to Montréal with an accessible new venue
Check out the full update: https://rustfoundation.org/media/rustconf-2026-early-details/
#rustlang #rustconf #rustconf26
Reinventing PCB Design & Routing with AI: The New Engineering Advantage
The dynamics of modern electronics demand design cycles that are faster, smarter, and significantly more resilient. At Hacktivate Network Solutions, we’re pushing that frontier by integrating AI-driven intelligence into PCB layout, routing, and optimization workflows—unlocking precision and throughput well beyond traditional methods.
Why AI Matters in PCB Design
PCB engineering is no longer just about connecting traces. Today’s boards must balance:
• Increasing layer density
• High-speed signal integrity
• Thermal constraints
• Power distribution accuracy
• EMC/EMI compliance
AI accelerates these constraints into real-time, data-driven decisions—removing hours (or days) of manual iteration.
AI-Powered Routing: Speed and Signal Integrity in Sync
Advanced routing engines now leverage machine learning to:
• Predict optimal trace paths based on current density, impedance, and crosstalk patterns
• Auto-correct layout conflicts as the design evolves
• Suggest alternative routing strategies to minimize via usage and reduce layer jumps
• Perform high-speed differential pair tuning automatically
• Optimize copper pours and thermal relief structures with precision
The result: cleaner, more reliable boards with higher electrical performance in a fraction of the time.
Predictive DFM/DFT Intelligence
By training AI on historical fab data, simulated failures, and manufacturability rulesets, designers get instant feedback on:
• Manufacturability risks
• Assembly bottlenecks
• Solder joint failure probability
• Component placement hotspots
• Compliance alignment (IPC, ISO, MIL-STD)
This transforms DFM/DFT from a late-stage check into a proactive design asset.
Closing the Loop with Simulation-Driven Optimization
AI-enhanced digital twins run thermal, electrical, and mechanical simulations continuously. This means:
• Faster validation
• Automated parameter sweeps
• Smarter thermal via placement
• Optimized power integrity profiles
PCB design becomes iterative and adaptive—guided by data, not trial-and-error.
What This Means for Engineering Teams
Organizations adopting AI-supported PCB design gain:
• Shorter development cycles
• Lower NRE and prototype costs
• Higher yield across manufacturing runs
• Better performance on first-pass builds
• Stronger reliability in mission-critical environments
For high-volume manufacturing, defense-grade systems, and enterprise-level hardware deployments, these advantages compound into a decisive competitive edge.
Hacktivate Network Solutions: Engineering at Machine Speed
We integrate AI into every layer of our PCB workflow—from schematic analysis to final routing automation—to deliver boards that are:
• Faster to market
• Built with higher electrical integrity
• Fully optimized for manufacturability and long-term reliability
This is PCB design without constraints—and the future of electronic innovation.
🚀 Exploring how AI is transforming PCB design, routing, and hardware engineering.
From automated signal-integrity routing to predictive DFM intelligence, I’m breaking down the tools and strategies shaping next-gen electronics.
🔧 If you’re into PCB design, AI-driven automation, cybersecurity, or advanced hardware workflows—follow me for ongoing insights from Hacktivate Network Solutions.
Let’s push the boundaries of what engineers can build. 💡✨
🚀 Exploring how AI is transforming PCB design, routing, and hardware engineering.
From automated signal-integrity routing to predictive DFM intelligence, I’m breaking down the tools and strategies shaping next-gen electronics.
🔧 If you’re into PCB design, AI-driven automation, cybersecurity, or advanced hardware workflows—follow me for ongoing insights from Hacktivate Network Solutions.
Let’s push the boundaries of what engineers can build. 💡✨
Reinventing PCB Design & Routing with AI: The New Engineering Advantage
The dynamics of modern electronics demand design cycles that are faster, smarter, and significantly more resilient. At Hacktivate Network Solutions, we’re pushing that frontier by integrating AI-driven intelligence into PCB layout, routing, and optimization workflows—unlocking precision and throughput well beyond traditional methods.
Why AI Matters in PCB Design
PCB engineering is no longer just about connecting traces. Today’s boards must balance:
• Increasing layer density
• High-speed signal integrity
• Thermal constraints
• Power distribution accuracy
• EMC/EMI compliance
AI accelerates these constraints into real-time, data-driven decisions—removing hours (or days) of manual iteration.
AI-Powered Routing: Speed and Signal Integrity in Sync
Advanced routing engines now leverage machine learning to:
• Predict optimal trace paths based on current density, impedance, and crosstalk patterns
• Auto-correct layout conflicts as the design evolves
• Suggest alternative routing strategies to minimize via usage and reduce layer jumps
• Perform high-speed differential pair tuning automatically
• Optimize copper pours and thermal relief structures with precision
The result: cleaner, more reliable boards with higher electrical performance in a fraction of the time.
Predictive DFM/DFT Intelligence
By training AI on historical fab data, simulated failures, and manufacturability rulesets, designers get instant feedback on:
• Manufacturability risks
• Assembly bottlenecks
• Solder joint failure probability
• Component placement hotspots
• Compliance alignment (IPC, ISO, MIL-STD)
This transforms DFM/DFT from a late-stage check into a proactive design asset.
Closing the Loop with Simulation-Driven Optimization
AI-enhanced digital twins run thermal, electrical, and mechanical simulations continuously. This means:
• Faster validation
• Automated parameter sweeps
• Smarter thermal via placement
• Optimized power integrity profiles
PCB design becomes iterative and adaptive—guided by data, not trial-and-error.
What This Means for Engineering Teams
Organizations adopting AI-supported PCB design gain:
• Shorter development cycles
• Lower NRE and prototype costs
• Higher yield across manufacturing runs
• Better performance on first-pass builds
• Stronger reliability in mission-critical environments
For high-volume manufacturing, defense-grade systems, and enterprise-level hardware deployments, these advantages compound into a decisive competitive edge.
Hacktivate Network Solutions: Engineering at Machine Speed
We integrate AI into every layer of our PCB workflow—from schematic analysis to final routing automation—to deliver boards that are:
• Faster to market
• Built with higher electrical integrity
• Fully optimized for manufacturability and long-term reliability
This is PCB design without constraints—and the future of electronic innovation.
RE: https://infosec.exchange/@Hacktivate/115581912020238418
🛰️ HACKTIVATE LABS // Current Ops
Actively building:
🔹 AI ReconX – adversarial AI + prompt security scanner
🔹 NetMapper – network discovery & visual intel
🔹 RedOrch – automated red team ops & reporting
🔹 LoRaMonitor – secure LoRaWAN mesh analytics
Testing fusion models: AI + Offensive Security.
If you’re building in #AIsec, #redteam, #DeFiSecurity, @mention me — let’s align signals.
More drops coming. Stay operational. ⚔️
🛰️ HACKTIVATE LABS // Current Ops
Actively building:
🔹 AI ReconX – adversarial AI + prompt security scanner
🔹 NetMapper – network discovery & visual intel
🔹 RedOrch – automated red team ops & reporting
🔹 LoRaMonitor – secure LoRaWAN mesh analytics
Testing fusion models: AI + Offensive Security.
If you’re building in #AIsec, #redteam, #DeFiSecurity, @mention me — let’s align signals.
More drops coming. Stay operational. ⚔️
RE: https://infosec.exchange/@Hacktivate/115582254829761849
⚠️ Most breaches don’t require genius — just opportunity.
Here’s what attackers actually exploit:
• Default creds still active
• Config drift no one monitors
• Cloud misconfigs after updates
• APIs exposed by accident
We’re building autonomous agents to close those gaps 24/7.
If you’re in #Cybersecurity #AIsec or #DevSecOps — let’s talk.
Tag a team that needs this operational.
🚨 I’m building something different.
Too many people “study cybersecurity” without developing real skill.
So we built a system based on *execution, documentation, and proof of work.*
Introducing:
🔐 120 Cybersecurity Projects — From Beginner to Advanced
Each lab builds a real capability:
🖥 Linux / Command Line
📡 Network Forensics & PCAP
🕵 OSINT & Threat Intel
⚔️ Red Team / Priv Escalation
🛡 Blue Team / SOC Defense
☁️ Cloud & IAM Security
🧠 AI + Threat Hunting
🧪 Malware & Reverse Engineering
📌 Every lab → becomes a GitHub/Notion portfolio entry
📌 Every submission → ranked on a leaderboard
📌 Proof of work > certifications
The INIT SEQUENCE (Beginner Labs) will be live soon !
Start with *5 labs* → earn your first badge 🟢
We don’t wait for permission.
We start building skill.
Join the ecosystem:
Send DM with your Discord username we will send info and invite with instructions on how to signup !
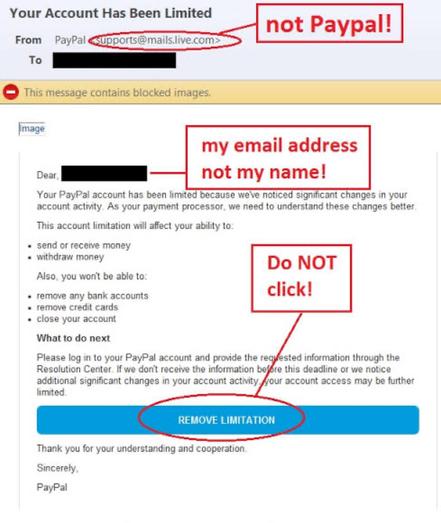
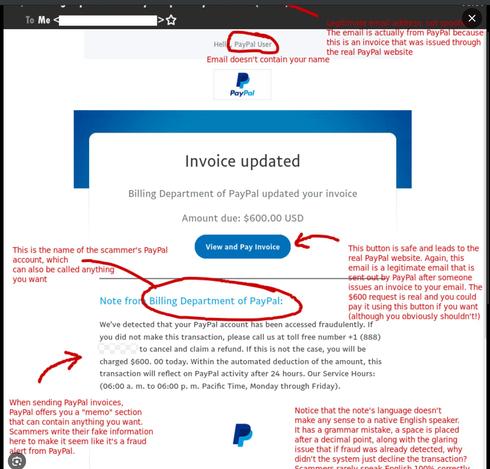
Has anyone received an email text or call regarding or attempting to scam your PayPal account?
#paypalscam #scamtracker #scambaiting #networksecurity #pentesting #HacktivateLabs
Has anyone received an email text or call regarding or attempting to scam your PayPal account?
#paypalscam #scamtracker #scambaiting #networksecurity #pentesting #HacktivateLabs
🚨 URGENT ALERT — New PayPal Scam Wave Is Spreading 🛡️
Cybercriminals are using highly realistic PayPal-themed scams to steal login credentials, 2FA codes, and even bank information.
These attacks are now appearing via email, SMS, phone calls, AND fake login pages.
The goal?
➡ Create panic.
➡ Make you click fast.
➡ Capture your identity & money.
⸻
🔎 What the Scam Looks Like
You may see messages like:
“Your account has been limited — verify now”
“Suspicious transaction detected — view invoice”
“Refund pending — login to confirm details”
These often link to fake PayPal pages designed to harvest credentials.
Some cases even include fake customer support phone numbers — leading to social engineering calls.
⸻
⚠️ Major Red Flags to Watch For:
🚩 Strange sender address (not @paypal.com)
🚩 Grammar/spelling mistakes
🚩 Links that don’t go to paypal.com
🚩 Requests for full password or 2FA code
🚩 Page doesn’t load when you manually type paypal.com
Reminder: Real PayPal will NEVER ask for your password or security code via email or SMS.
⸻
🛡️ If You Receive a Suspicious Message
✔ Do NOT click any links
✔ Open a browser & type paypal.com yourself
✔ Check your recent activity directly
✔ Enable / reset 2FA & change your password
✔ Remove any suspicious linked cards/banks
✔ Report emails to: phishing@paypal.com
✔ Contact your bank if money was moved
⸻
🔐 Prevention Steps
✔ Use a unique, strong password
✔ Enable multi-factor authentication
✔ Keep your devices updated
✔ Use official app — avoid random links
✔ Never trust “urgent” calls claiming to be PayPal
✔ Treat every login page as a security check
⸻
🧠 Most Common Scam Variants Right Now
⚙ Fake “account suspension” warnings
📨 Invoice phishing scams
📞 Phone-based support scams (TOAD)
🌐 Fake login portals / cloned pages
🔒 Credential stuffing from old data breaches
⸻
Spread awareness — this is actively circulating.
One share could protect someone’s money and identity.
👇 Let’s talk:
Which red flag do YOU think is easiest to miss?
#infosec #scams #paypalScam #PayPalScam
#ScamAlert
#FraudPrevention
#PhishingWarning
#IdentityTheft
#AccountSecurity
#StopScammers
#OnlineScams
#CyberFraud
For educational & defensive purposes only.
No personal accounts can be investigated — always contact PayPal directly for help.
🔍 Top 21 Dark-Web Resources & Tools for OSINT Professionals
For authorized, legal & ethical investigations only 🛡️
# Resource / Tool What It’s Useful For
1 Tor Browser / Hidden-Network Access The fundamental gateway to dark-web (.onion) access — necessary for all hidden-service research. 
2 Ahmia Search-engine for .onion sites — helps locate indexed hidden-web content when you start. 
3 OnionScan Scans hidden services for vulnerabilities, service metadata — useful for vetting onion links or threat-monitoring. 
4 Darkus Onion-link discovery / hidden-service enumeration — helps find less obvious or new onion domains. 
5 DarkOwl Vision / Dark-Web Intelligence Feeds Commercial-grade intelligence — monitors dark-web chatter, leaked databases, posts, and marketplaces. 
6 Hunchly OSINT tool that supports dark-web investigations + audit trails — ensures captured intel is documented, tamper-evident. 
7 SL Crimewall Aggregated OSINT platform covering dark-web + surface web for threat actors, leaks, fraud data. 
8 Silo for Research Sandbox-oriented dark-web browsing / data collection — reduces risks when researching hidden services. 
9 Intelligence X Hybrid tool: surface + deep web + leak-data archive — can expose previously compromised credentials, email dumps, etc. 
10 Darkdump / Onion-Dump Tools & Archives Dump retrieval, database leak hunting — good for researching breach data and historical leaks. 
11 Community-Curated Link Indexes (e.g. Onion-link lists, “The Hidden Wiki” style indexes) Starting point for exploratory OSINT or leak mapping — but must be vetted carefully to avoid traps. 
12 Dark-Web Market & Forum Monitoring (various hidden markets & forums) Intelligence on illicit trades, stolen data, threat-actor communication, zero-day/job boards for malware, and more. 
13 Leak / Breach Data Aggregators (on darknet + surface web) Useful for credential stuffing detection, breach exposure checks, early leak detection. 
14 Vulnerability / Exploit Sale Monitoring Channels on Dark Web Early warnings on potential zero-days or exploit kits circulating among adversaries. 
15 Dark-Web Archive Snapshots (for safe offline review) Prevents exposure to active malware — allows analysts to snapshot & inspect content in isolated environments. 
16 Hybrid Crawlers (surface + deep + dark web) for IoT & Threat Intelligence For comprehensive threat coverage across all web layers — helps link darknet chatter to real-world infrastructure signals. 
17 OSINT Framework (for methodology & resource classification) Helps structure investigations — combining dark web findings with surface-web OSINT methodology.

18 Closed-source / Enterprise CTI Platforms with Dark Web Feeds For teams needing scalable, reliable, and safe dark-web monitoring + alerting + compliance audit trails. 
19 Secure Sandbox & VM Environments for Dark-Web Access Crucial for operational security — avoids device compromise, protects identity, avoids leaks & traceability. 
20 Human-Intelligence & Forum Surveillance (Forums, Chatrooms, Community Monitoring) Sometimes leads, rumors or chatter surface on forums before leaks — early warning for upcoming campaigns or data dumps. 
21 Cross-Layer Correlation: Combine Dark Web + Surface Web OSINT + Historical Leak Data Builds comprehensive, multi-dimensional threat intelligence — links online identity, breach history, activity patterns. 
📚 Why OSINT Pros Use the Dark Web — What Makes It Critical
• Hidden Info ≠ Indexed: Many leaks, exploit sales, stolen credentials, or threat-actor communications live only on darknet services — invisible to regular search engines. 
• Early Detection & Proactive Defense: Monitoring marketplaces and forums can flag exploited data or emerging malware/exploit kits before they hit mainstream — crucial for risk mitigation. 
• Deeper Threat Actor Insight: Profiles, communication patterns, vendor listings, zero-day discussions — all visible in certain dark-web venues, giving unique context on threat capabilities. 
• Leak & Data-Sale Visibility: Credentials, PII, internal data dumps — selling underground before breach disclosure. Knowing early can save companies & individuals. 
• Complement to Surface OSINT: Dark web data fills gaps — what doesn’t show up in public records may exist in hidden commerce, hacker forums or leak archives. 
⸻
⚠️ Warning: Risks & Best Practices
Before you step into darknet OSINT, these are mandatory pre-conditions for safety and legality:
• Use dedicated VM or sandbox machine — never your main workstation. 
• Always follow legal, organizational, and compliance policies — unauthorized data access is a legal & ethical minefield. 
• Only gather publicly allowed content — no hacking, no exploitation, no unauthorized access.
• Verify all data — darknet = noise + scams + misinformation. Cross-check with multiple sources. 
• Maintain OPSEC — use VPN + Tor, clear session data, avoid downloadable files, don’t reuse identifiers. 
⸻
🔦 OSINT & Cybersecurity Professionals — If you’re not using the Dark Web in your intelligence stack, you’re missing real data.
✅ I compiled a **Top 21 Dark-Web Tools & Resources** — from onion link search engines to leak-archives, exploit monitoring, and closed-source feeds.
🚨 This isn’t for trolling. It’s for threat-intel, leak-monitoring, breach detection, and proactive defense.
**Important:** Only access darknet content via sandboxed / isolated environments. Follow legal & ethical guidelines, and treat all findings as unverified until cross-checked.
Want the full resource sheet + quick-start guide? Drop a comment or DM.
#CyberSecurity #OSINT #DarkWeb #ThreatIntel #Infosec #DataBreach #DigitalForensics #SecurityResearch
Server Security Checklist — Essential Hardening Guide
Securing your servers isn’t optional — it’s your first line of defense against data breaches, ransomware, insider threats, and lateral movement. Use this checklist as a baseline for Linux, Windows, cloud, hybrid, or on-prem servers.
⸻
🔧 1. System & OS Hardening
• Keep OS & packages updated (apply security patches frequently).
• Remove / disable unused services & software.
• Enforce secure boot + BIOS/UEFI passwords.
• Disable auto-login and guest accounts.
• Use minimal OS images only (reduce attack surface).
⸻
🔐 2. Access Control
• Enforce strong passwords & MFA everywhere.
• Use RBAC & least privilege access.
• Disable root/Administrator login over SSH/RDP.
• Rotate credentials & keys regularly.
• Implement just-in-time access for privileged users.
⸻
🌐 3. Network Security
• Restrict inbound/outbound traffic via firewalls.
• Segment critical servers from general LANs/VLANs.
• Disable unused ports & protocols.
• Enable DoS/DDoS protection.
• Apply zero-trust network principles.
⸻
🔑 4. Secure Remote Access
• Use SSH key-based authentication (disable password login).
• Enforce VPN for admin access.
• Log & monitor all remote access sessions.
• Disable legacy protocols (Telnet, FTP, SMBv1).
• Require bastion/jump host for critical access.
⸻
📊 5. Logging & Monitoring
• Enable centralized logging (syslog / SIEM).
• Track failed login attempts & anomalies.
• Configure alerts for privilege escalation or config changes.
• Monitor log tampering.
• Retain logs securely for audits & forensics.
⸻
🔒 6. Data Protection
• Encrypt data at rest (LUKS, BitLocker, etc.).
• Encrypt data in transit (TLS 1.2+).
• Strict database access policies.
• Regular, offline, immutable backups.
• Test restore procedures (don’t assume backups work).
⸻
🔁 7. Application & Patch Management
• Keep middleware, frameworks, and apps patched.
• Delete default credentials & sample files.
• Enable code signing for software packages.
• Use secure coding practices (OWASP Top 10).
• Implement dependency scanning (Snyk, Trivy, etc.).
⸻
🛡️ 8. Malware & Intrusion Defense
• Deploy EDR/AV on endpoints.
• Enable IDS/IPS at network edge.
• Automatic vulnerability scans (schedule weekly/monthly).
• Monitor persistence techniques (cron, startup scripts).
• Block known malicious IP ranges & TLDs.
⸻
🏢 9. Physical & Cloud Security
• Restrict physical access to server racks/rooms.
• Enable provider security tools (AWS Security Groups, Azure NSG, IAM).
• Harden cloud images (CIS benchmarks).
• Review cloud logging & audit trails regularly.
• Disable unused cloud API keys / roles.
⸻
📜 10. Policy & Compliance
• Use CIS / NIST / ISO-27001 benchmarks.
• Track & document every access change.
• Force annual access reviews & key rotation.
• Perform regular security training for admins.
• Maintain disaster recovery & incident plans.
⸻
➕ Additional 5 Critical Controls (Advanced Hardening)
🧠 11. Privileged Access Management (PAM)
• Use jump hosts & session recording.
• Just-In-Time access for admins.
• Store keys in secure vaults (HashiCorp Vault, CyberArk).
🚨 12. Real-Time Threat Detection
• Use behavioral analytics → UEBA/XDR.
• AI-based anomaly detection recommended.
• Block suspicious IPs automatically.
🧪 13. Red Team & Pentesting
• Run regular internal pentests.
• Validate configuration weaknesses.
• Simulate phishing + lateral movement scenarios.
🧱 14. Container / VM Isolation
• Use AppArmor, SELinux, Seccomp profiles.
• Limit Docker socket access & root containers.
• Scan images before deployment.
📦 15. Automated Configuration Management
• Use IaC (Terraform, Ansible, Puppet) for repeatable and secure builds.
• Detect drift using compliance scanning.
• Version control all infrastructure.
⸻
🧠 Core Reminder
A server is only as secure as the team who maintains it.
Hardening isn’t one task — it’s an ongoing
#ServerSecurity #SystemHardening #InfoSec #CyberSecurity #BlueTeam
#DevSecOps #SysAdmin #ThreatDetection #AccessControl #NetworkSecurity
#LinuxSecurity #SecureArchitecture #RiskMitigation #SecurityChecklist
#CloudSecurity #InfrastructureSecurity #ZeroTrust #SecurityMonitoring
A programmer-friendly I/O abstraction over io_uring and kqueue (2022)
Link: https://tigerbeetle.com/blog/2022-11-23-a-friendly-abstraction-over-iouring-and-kqueue/
Discussion: https://news.ycombinator.com/item?id=46073817
RE: https://mastodon.online/@CuriousGoblin/115627690640062906
After weathering the storm of the U.S. tariffs, the @CuriousGoblin studio is finally finding its rhythm again. Things are tidied, clearer, more focused. And the first sign of calm after the chaos? We’re back to doing what we love: launching new products in our shop.
@lamedianation @cryptoheadhunter #dappstorekit #












![4 PENEE——— eee
2 \ A fu < 7 7 7 ee =
- AR ; 4 = " pi i — T :
— ER ~~ ; BR (§ go | | |
fe a gg 7 i x Ve : Es Fe | :
(Sieh | SL ENON | Ta Cl rs {
| ee 1B) AW \\ THR el Al
| p_ gt LF mn {hs
; | . : / 5
1
\\ . - bs
| : r= oo a |
rt p+ ae" oy a ' Pi Em it
i BE p. = g «Pe L
J a y &¥ 3 \ L.
| go AN % DW
i . . \ ig i
: eee 5; j / 4 z Sh. \,
] = — i — - a
Sy os
”~ “= ay am —
-](https://files.mastodon.social/cache/media_attachments/files/115/627/868/944/616/043/small/bb09806ae54c194e.jpeg)


![Basic Server Iy pes
Origin y Proxy Mail _,
5 ) 5
* Listens for incoming * os EEL * Controls the Sending _SNf—d5
inbernet requests ond cecewing of email («8
gos ht © Tntermediole Servers between cient and ongn | ® Receives mail From fay 7
Clients
Act as oddihonal Securiky, caching senices,
Delivers web content Fo Clients ® by, Caching El
© | pass requests on bo other servers odministrahve control, and more * Delors mal Jo Hoe
1 does nek have he capacity to respond Computers
we Web DNS Got gr
nl ® Transhbes domain names ink
E==g==VeaN ® oa bid pss lic IP addresses v
g espe ses
a ®fcks like an IP address book.
[BN] © Communicates with web browsers For the mlernel
—
I Can Store and prokeck web ® Includes server Sub-Fypes such as Rook servers,
dic = 4 Hea Authoribakive Nome Servers, and Resolver servers](https://files.mastodon.social/cache/media_attachments/files/115/627/867/613/151/631/small/12701c44703d2066.jpeg)
